p4 protect
Synopsis
Control users' access to files, directories, and commands.
Syntax
p4 [g-opts] protect
p4 [g-opts] protect -o
p4 [g-opts] protect -i
Description
Use p4 protect to control Perforce permissions. You can use p4 protect to:
-
Control which files particular users can access
-
Manage which commands particular users are allowed to use
-
Combine the two, allowing one user to write one set of files but only be able to read other files
-
Grant permissions to groups of users, as defined with p4 group
-
Grant or deny specific access rights to users by using the
=read,=open,=write, and=branchrights, without having to re-grant lesser permissions -
Limit access to particular IP addresses, so that only users at these IP addresses can run Perforce.
In general, you typically grant an access level to a user or group, after which, if finer-grained control is required, one or more specific rights can then be selectively denied.
The permission levels and access rights are described in the table below:
|
Permission Level / Right |
What the User Can Do |
|---|---|
|
|
The user can access all Perforce metadata, but has no access to file contents. The user can run all the commands that describe Perforce objects, such as p4 files, p4 client, p4 job, p4 describe, p4 branch, etc. |
|
|
The user can do everything permitted with
|
|
|
If this right is denied, users cannot use p4 print, p4 diff, or p4 sync on files. |
|
|
This gives the user permission to do everything she can do with
|
|
|
If this right is denied, users cannot open files with p4 add, p4 edit, p4 delete, or p4 integrate. |
|
|
The user can do all of the above, and can also write files with p4 submit and lock them with p4 lock. |
|
|
If this right is denied, users cannot submit open files. |
|
|
If this right is denied, users cannot use files as a source for p4 integrate. |
|
|
This permission is meant for external programs that access
Perforce. It gives the external programs permission to do
anything that |
|
|
Includes all of the above, including administrative commands that override changes to metadata, but do not affect service operation. These include p4 branch -f, p4 change -f, p4 client -f, p4 job -f, p4 jobspec, p4 label -f, p4 obliterate, p4 shelve -f -d, p4 typemap, p4 unlock -f, and p4 verify. |
|
|
Includes all of the above, plus access to the superuser commands such as p4 admin, p4 counter, p4 triggers, p4 protect, the ability to create users with p4 user -f, and so on. |
Form Fields
When you run p4 protect, Perforce displays a form with
a single field, Protections:. Each permission is
specified in its own indented line under the
Protections: header, and has five values:
|
Column |
Description |
|---|---|
|
Access Level |
One of the access levels |
|
User or Group |
Does this protection apply to a |
|
Group Name or User Name |
The name of the user or the name of the group, as defined by
p4 group. To
grant this permission to all users, use the |
|
Host |
The IP address of the client host. IPv6 addresses and IPv4
addresses are also supported. You can use the
If you use the
How the system forms host addresses depends on the setting of
the
Setting the |
|
Depot File Path |
The depot file path this permission is granted on, in Perforce depot syntax. The file specification can contain Perforce wildcards.
To exclude this mapping from the permission set, use a dash
( If a depot is excluded, the user denied access will no longer see the depot in the output of p4 depots. Nor will the depot show up, for this user, in the default branch, client, and label views. |
When exclusionary mappings are not used, a user is granted the highest permission level listed in the union of all the mappings that match the user, the user's IP address, and the files the user is trying to access. In this case, the order of the mappings is irrelevant.
When exclusionary mappings are used, order is relevant: the exclusionary mapping overrides any matching protections listed above it in the table. No matter what access level is being denied in the exclusionary protection, all the access levels for the matching users, files, and IP addresses are denied.
If you use exclusionary mappings to deny access to an area of the depot to
members of group1, but grant access to the same area of
the depot to members of group2, a user who is a member
of both group1 and group2 is either
granted or denied access based on whichever line appears last in the
protections table.
Options
|
|
Read the form from standard input without invoking an editor. |
|
|
Write the form to standard output without invoking an editor. |
|
|
See “Global Options”. |
Usage Notes
|
Can File Arguments Use Revision Specifier? |
Can File Arguments Use Revision Range? |
Minimal Access Level Required |
|---|---|---|
|
No |
No |
|
-
Each permission level includes all the access levels below it, as illustrated in this chart:
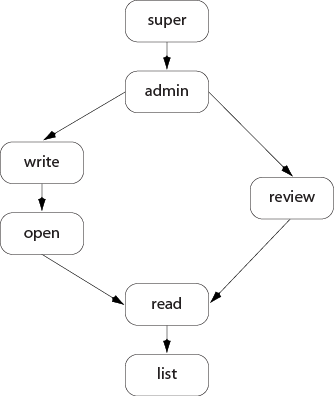
-
The specific rights of
=read,=open,=write, and=branchcan be used to override the automatic inclusion of lower access levels. This makes it possible to deny individual rights without having to then re-grant lesser rights.For example, if you want administrators to have the ability to run administrative commands, but to deny them the ability to make changes in certain parts of the depot, you could set up a permissions table as follows:
admin user joe * //... =write user joe * -//depot/build/... =open user joe * -//depot/build/...
In this example, user
joecan perform administrative functions, and this permission applies to all depots in the system. Because theadminpermission level also implies the granting of all lower access levels,joecan also write, open, read and list files anywhere in the system, including//depot/build/. To protect the build area, the=writeand=openexclusionary lines are added to the table. Userjoeis prevented from opening any files for edit in the build area. He is also prevented from submitting any changes in this area he may already have open. He can continue to create and modify files, but only if those files are outside of the protected//depot/build/...area. -
Access levels determine which commands you can use. The following table lists the minimum access level required for each command. For example, because p4 add requires at least
openaccess, you can run p4 add if you haveopen,write,admin, orsuperaccess.Command
Access Level
Notes
add
openadmin
superannotate
readarchive
adminattribute
writeThe
-foption to set the attributes of submitted files requiresadminaccess.branch
openThe
-foption to override existing metadata or other users' data requiresadminaccess.branches
listchange
openThe
-ooption (display a change on standard output) requires onlylistaccess. The-foption to override existing metadata or other users' data requiresadminaccess.changes
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
client
listThe
-foption to override existing metadata or other users' data requiresadminaccess.clients
listconfigure
supercopy
listlistaccess to the source files;openaccess to the destination files.counter
reviewlistaccess to at least one file in any depot is required to view an existing counter's value;reviewaccess is required to change a counter's value or create a new counter.counters
listcstat
listdbschema
superdbstat
superdbverify
superdelete
opendepot
superThe
-ooption to this command, which allows the form to be read but not edited, requires onlylistaccess.depots
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
describe
readThe
-soption to this command, which does not display file content, requires onlylistaccess.diff
readdiff2
readdirs
listdiskspace
superedit
openexport
superfilelog
listfiles
listfix
openfixes
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
flush
listfstat
listgrep
readgroup
superThe
-ooption to this command, which allows the form to be read but not edited, requires onlylistaccess.The
-aoption to this command requires onlylistaccess, provided that the user is also listed as a group owner.The
-Aoption requiresadminaccess.groups
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
have
listhelp
noneinfo
noneintegrate
openThe user must have
openaccess on the target files andreadaccess on the source files.integrated
listinterchanges
lististat
listjob
openThe
-ooption to this command, which allows the form to be read but not edited, requires onlylistaccess.The
-foption to override existing metadata or other users' data requiresadminaccess.jobs
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
journaldbchecksums
superkey
reviewlistaccess to at least one file in any depot is required to view an existing key's value;reviewaccess is required to change a key's value or create a new key.key
listadminaccess is required if thedm.keys.hideconfigurable is set to2.keys
listadminaccess is required if thedm.keys.hideconfigurable is set to1or2.label
openThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
The
-foption to override existing metadata or other users' data requiresadminaccess.labels
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
labelsync
openlicense
superThe
-uoption, which displays license usage, requires onlyadminaccess.list
openlock
writelockstat
superlogappend
listlogger
reviewlogin
listlogout
listlogparse
superlogrotate
superlogschema
superlogstat
superlogtail
supermerge
openmonitor
listsuperaccess is required to terminate or clear processes, or to view arguments.move
openobliterate
adminopened
listpasswd
listping
adminpopulate
openprint
readprotect
superprotects
listsuperaccess is required to use the-a,-g, and-uoptions.property
listlistto read,adminto add/delete new properties, or show a property setting for all users and groups.proxy
noneMust be connected to a Perforce Proxy
pull
superreconcile
openreload
openadminaccess is required to use p4 reload -f to reload other users' workspaces and labels.reopen
openreplicate
superresolve
openresolved
openrestore
adminrevert
listreview
reviewThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
reviews
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
server
superserverid
listsuperaccess is required to set the server ID.set
noneshelve
openadminaccess is required to forcibly delete shelved files with p4 shelve -f -dsizes
liststatus
openstream
openstreams
listsubmit
writesync
readtag
listtickets
nonetriggers
supertypemap
adminThe
-ooption to this command, which allows the form to be read but not edited, requires onlylistaccess.unload
openadminaccess is required to use p4 unload -f to unload other users' workspaces and labels.unlock
openThe
-foption to override existing metadata or other users' data requiresadminaccess.unshelve
openupdate
listuser
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
The
-foption (which is used to create or edit users) requiressuperaccess.users
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
If the
run.users.authorizeconfigurable is set to1, you must also authenticate yourself to the server before you can run p4 users.verify
adminwhere
listThis command doesn't operate on specific files. Permission is granted to run the command if the user has the specified access to at least one file in any depot.
-
At a new Perforce installation, anyone who wants to use Perforce is allowed to connect to the service, and all Perforce users are superusers. The first time anyone runs p4 protect, the invoking user is made the superuser, and everyone else is given
writepermission on all files. Run p4 protect immediately after installation. -
In the course of normal operation, you'll primarily grant users
list,read,write, andsuperaccess levels. Theopenandreviewaccess levels are used less often. -
Those commands that list files, such as p4 describe, will only list those files to which the user has at least
listaccess. -
Some commands (for instance, p4 change, when editing a previously submitted changelist) take a
-foption that requiresadminorsuperaccess. -
The
openaccess level gives the user permission to change files but not submit them to the depot. Use this when you're temporarily freezing a codeline, but don't want to stop your developers from working, or when you employ testers who are allowed to change code for their own use but aren't allowed to make permanent changes to the codeline. -
The
reviewaccess level is meant for review daemons that need to access counter values. -
If you write a review daemon that requires both
reviewandwriteaccess, but shouldn't havesuperaccess, grant the daemon bothreviewandwriteaccess on two separate lines of the protections table. -
To limit or eliminate the use of the files on a particular server as a remote depot from another server (as defined by p4 depot), create protections for user
remote(or for the service user by which the other server authenticates itself). Remote depots are accessed either by the service user associated with the user's Perforce service, or by a virtual user namedremote. -
For further information, see the "Protections" chapter of the Perforce Server Administrator's Guide: Fundamentals.
Examples
Suppose that user joe is a member of groups
devgroup and buggroup, as set by
p4 group, the
organization is using only IPv4 connections, and the protections table
reads as follows:
super user bill * //... write group devgroup * //depot/... write group buggroup * -//depot/proj/... write user joe 192.168.100.0/24 //...
Joe attempts a number of operations. His success or failure at each is described below:
|
From IP address... |
Joe tries... |
Results |
|---|---|---|
|
|
p4 print //depot/misc/... |
Succeeds. The second line grants Joe |
|
|
p4 print //depot/proj/README |
Fails. The third line removes all of Joe's permissions on any files in this directory. (If the second protection and the third protection had been switched, then the subsequent protection would have overridden this one, and Joe would have succeeded). |
|
|
p4 print //depot/proj/README |
Succeeds. Joe's workstation is at an IP address from which he is granted this permission in the fourth line. |
|
|
p4 verify //depot/misc/... |
Fails. p4
verify requires |