Helix TeamHub SSH
Use a bot account instead of personal credentials to store the SSH public key required for the GitConnector. (The web-service-user mentioned below).
The two options are:
- Use a regular bot, and give it access to relevant projects and repositories on the team view
- Use a company admin bot account, which has access to every repository inside the company
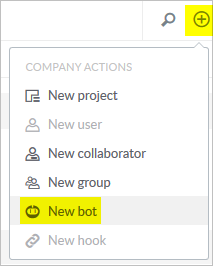
For more information, see Bots & programmatic repository access in Helix TeamHub User Guide.
The target repo must NOT already exist in Helix Server.
The source repo must not be empty.
-
On the Git Connector server, log in as the
rootuser. - Create a
.sshdirectory:mkdir /var/www/.ssh - Assign the owner of the directory to be the
web-service-user:chown web-service-user:gconn-auth /var/www/.ssh -
Switch user from
rootto theweb-service-user:Ubuntu CentOS su -s /bin/bash - www-datasu -s /bin/bash - apacheand generate the public and private SSH keys for the Git Connector instance:
ssh-keygen -t rsa -b 4096 -C web-service-user@gitConnector.comthen follow the prompts.
- Locate the public key:
/var/www/.ssh/id_rsa.pub -
Copy this public key to the GitLab or GitHub server and add
/var/www/.ssh/id_rsa.pubto the user account (helix-user) that performs clone and fetch for mirroring. - Configure the webhook for mirroring:
- Set the environment variable
GCONN_CONFIGto the absolute path to thegconn.conffile:export GCONN_CONFIG=/opt/perforce/git-connector/gconn.conf - Add the web hook:
gconn --mirrorhooks add graphDepotName/repoName git@HelixTeamHubServer/companyName/projects/projectName/repositories/gitrepoNamewhere access-token:secret represents your personal access token for GitHub or GitLab.
- Save the secret token that the
--mirrorhookscommand generates.
Copy the URL from your project's SSH drop-down box.
The secret token is also stored in /opt/perforce/git-connector/repos/graphDepotName/repoName.git/.mirror.config
Mirror a repo over SSH
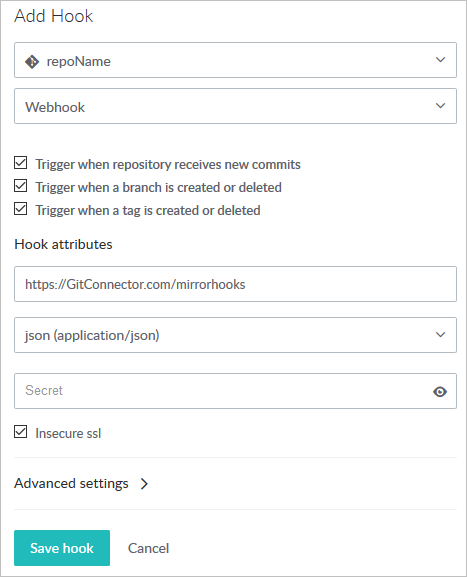
-
Select Hooks, Add Hook, and select a repository from the drop-down.
- Select service WebHook from the drop-down
- Check the triggers that you want to launch a mirroring action
- Under Hook attributes:
- Paste the URL of the Git Connector into the URL text box:
https://GitConnector.com/mirrorhooks - Select content-type of json (application/json) from the drop-down.
- Paste the mirrorhook secret token in the Secret text box.
- Check the Insecure ssl checkbox because no certificate is associated with the webhook.
- Paste the URL of the Git Connector into the URL text box:
-
Click Save hook.
- Validate that mirroring is in place by running the following command on the Git Connector:
gconn --mirrorhooks listThis displays the repositories that are mirrored and the Git Host. For example:
gconn --mirrorhooks list
//hth/repoName <<< http://HelixTeamHub.com/hth/projects/projectName/repositories/git/repoName.git ...
//hth/repoName2 <<< http://HelixTeamHub.com/hth/projects/projectName/repositories/git/repoName2.git ... Not mirrored by this Gconn instance ( no mirror config )
Troubleshooting
If there are any issues, review the following files, or send them to Perforce Technical Support:
Helix TeamHub log at /var/log/hth/resque/current
and from the Git Connector:
/opt/perforce/git-connector/repos/graphDepot/repoName.git/.mirror.config
/opt/perforce/git-connector/repos/graphDepot/repoName.git/push_log
/opt/perforce/git-connector/repos/graphDepot/repoName.git/fetch_log
/opt/perforce/git-connector/repos/graphDepot/repoName.git/.mirror.log
/opt/perforce/git-connector/gconn.conf
/opt/perforce/git-connector/logs/gconn.log
/opt/perforce/git-connector/logs/p4gc.log