LDAP authentication
LDAP is one of the most commonly used application protocols for accessing and maintaining corporate user directories. Helix TeamHub can be configured to use corporate LDAP for authentication. Once LDAP authentication is enabled, all successful login attempts either create a new TeamHub user or update an existing one along with the LDAP group information. The configuration process is explained below.
If Helix authentication is the selected method of authentication and the Helix Server uses LDAP authentication, there is no need to use LDAP authentication in TeamHub. Authentication requests from TeamHub are parsed to Helix Server, which then connects to the LDAP/AD server to perform the authentication for the user. Note that LDAP authentication on the Helix Server side must be established using the LDAP specification method (for details, see Authenticating against Active Directory and LDAP servers section in the Helix Core Server Administrator Guide).
Configuring LDAP authentication
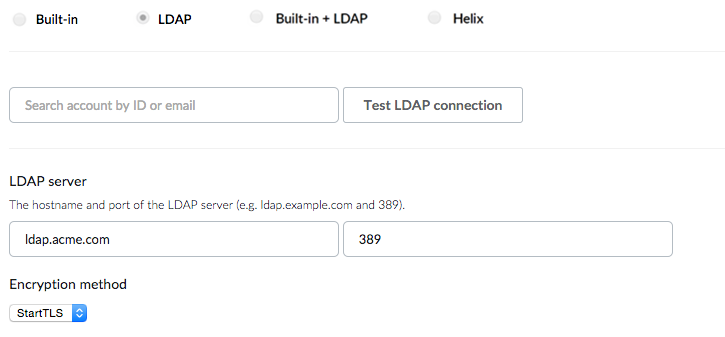
To enable LDAP authentication, browse to TeamHub Admin at http(s)://[hostname]/admin. From the Admin pane, click on the Preferences link in the navigation bar.
Choose the LDAP authentication option and specify the hostname and port of the LDAP server. The hostname might use a URL like ldap.acme.com or an IP like 10.0.0.30. The port of the LDAP server might vary depending on the connection type. For secure communication between TeamHub and the LDAP server, choose either StartTLS or LDAPS encryption method.
Select Both as the authentication option to create local TeamHub users while still using LDAP authentication. Note that once Both is enabled, all TeamHub users will be able to set their local passwords and TeamHub will only attempt to bind to LDAP when built in authentication is unsuccessful.
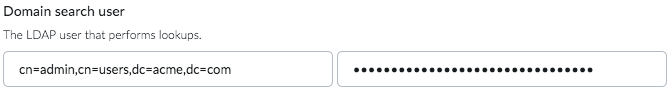
The Domain search user performs lookups to authenticate other accounts when users sign in. The Domain search user is typically a service account used specifically for third-party integrations. For the Domain search user, only read-access to LDAP is needed.
Use the fully qualified user name, which would look something like this: cn=admin,cn=Users,dc=acme,dc=com.
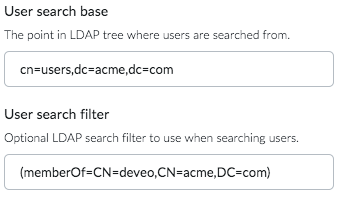
The User search base function specifies the fully qualified name of the starting point in the LDAP tree to search for users. If no search filters are specified, then the User search base will retrieve the entire data set.
A user search filter can be used to specify conditions that must be met for a record to be included when searching for users. This setting is optional.
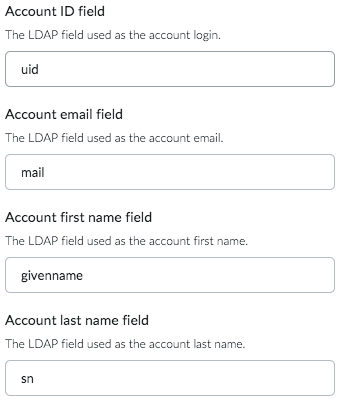
The Account ID field is the name of the LDAP attribute used as the account login. For most Active Directory installations this will be sAMAccountName. For other LDAP solutions like OpenLDAP, the value of this field is usually uid.
The Account email field is the name of the LDAP attribute used as the account email. Usually the value of this field is mail.
The Account first name and last name fields are optional.
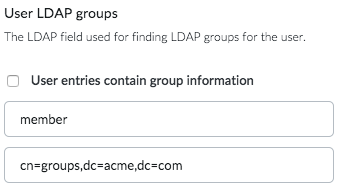
The User LDAP groups field is the name of the LDAP attribute used for finding LDAP groups for a user. Check User entries contain group information if the directory allows finding LDAP group information directly from user entries. The name of the LDAP field is commonly memberOf.
Otherwise set the value of the field to either member, uniqueMember or memberUid depending on the LDAP schema, and set the base path where to search for groups. Nested group support can be enabled for Active Directory by using member:1.2.840.113556.1.4.1941: as a value for the field.
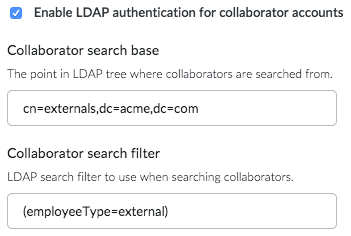
Collaborators use built-in authentication by default. LDAP authentication can also be enabled for collaborators by using a different search base or search filter from normal users. Use the Test LDAP connection feature to search for a user and a collaborator account, and make sure it returns only either a user or a collaborator.
If using Helix TeamHub LDAP Sync application to keep user details up-to-date, enter the unique LDAP source identifier and also add it to the LDAP sync configuration file. Once configured, TeamHub will keep the newly created account details in sync with this LDAP.
Finally, use the Test LDAP connection feature to test the validity of the configuration. Enter an email or ID of an account and verify that correct results are returned.
Further Integration
To go even further with integrating the TeamHub installation to the corporate LDAP, consider keeping user accounts in sync with Helix TeamHub LDAP Sync application.
Caveats
When changing the authentication method back from LDAP to built-in, all users that have been created via LDAP will need to perform a password reset to login again. After the authentication method changes, users will not be able to edit any user attributes that were originally synced from LDAP (e.g. username, email and password).