Installing
There are four ways to install Helix Authentication Service as an application, plus the alternative of installing HAS as a Windows service.
Prerequisites
- Administrative expertise with the software of your Identity Provider
- Expertise in security administration sufficient to work with both your Identity Provider (IdP) and your Perforce server product.
-
A web browser. Any client using the authentication service requires a web browser.
- Source code for Helix Authentication Service from the Downloads page (or from the GitHub repository).
-
Any client (even the p4 command-line client) is still required to authenticate through your IdP's website. We recommend that at least one user with super level access use Helix Core Server authentication instead of Helix Authentication Service. See the Authorizing Access in the Helix Core Server Administrator Guide.
-
Two valid certificates:
-
a server certificate for HAS
-
a client certificate for the other half of the solution, such as:
-
Helix Core Server Extension
-
Helix Swarm
-
Helix ALM License Server
-
Helix Plan Server (formerly known as Hansoft Server)
-
-
- One or more of the following:
-
You must have knowledge of Helix Core administration for authentication with tickets - see Authenticating using passwords and tickets in the Helix Core Server Administrator Guide.
- To configure Helix Authentication Service for Helix Core Server (P4D) and a Helix Core client, such as the Helix Core Visual client (P4V) or Helix Sync, you must configure a Helix Core Server Extension. See the Administrator's Guide for Helix Authentication Extension in the docs directory of the Helix Authentication Extension repository on GitHub.
-
The Helix Authentication Extension provides a mechanism to test the Helix Authentication Service with a select group of users prior to rolling out the service organization-wide. See the Testing the extension section in the Administrator's Guide for Helix Authentication Extension in the
docsdirectory of the Helix Authentication Extension repository on GitHub.
| Helix Core Server, version 2019.1 or later |
Important
|
|
Helix ALM, version 2019.4 or later, or Surround SCM, version 2019.2 or later |
Important
To use the Helix Authentication Service to authenticate from Helix ALM or Surround SCM, you must configure Helix ALM License Server. see the Helix ALM License Server Admin Guide. |
| Hansoft Server 11.0 or later | See Integrating with identity providers for single sign-on in the Hansoft System Administrator Guide |
To understand the flow of information between the IdP, HAS, and the component that represents the product server, see the diagrams that applies for you:
If you want to use multi-factor authentication (MFA) with the Helix Authentication Service, consider using the multi-factor authentication solution provided by your IdP.
We do NOT recommend using the Helix MFA Authenticator with Helix Authentication Service. The Helix MFA Authenticator should only be implemented when your password store and MFA service are separated. The typical use case for the Helix MFA Authenticator is to have an on-prem password store (such as LDAP) and a cloud-based MFA service.
Four ways to install HAS as an application
You can install Helix Authentication Service (HAS) as an application by using any of the following:
| Docker |
The easiest option is the pre-build Docker container for download. For more information, see https://hub.docker.com/r/perforce/helix-auth-svc |
|
|
The next easiest option is the package installation. Supported operating systems for package installation
|
|
|
Supported operating systems for the installation script
|
|
|
Supported operating systems for manual installation
Requires an installation of:
|
Package installation
If your operating system is one of the Supported operating systems for package installation, perform the package installation because it allows you to use the YUM or APT package manager.
Package installation requires sudo or root level privileges.
A package installation creates an operating system user account named perforce and a group named perforce for running HAS. Do not run HAS with the Linux root user account or a Windows administrator account.
-
Follow the instructions for how to configure APT or YUM repositories at Perforce Packages.
-
Install the
helix-auth-svcpackage:
-
For APT, run
sudo apt-get install helix-auth-svcAlternatively, browse the repository and download a Deb file directly from https://package.perforce.com/apt/
-
For YUM, run
sudo yum install helix-auth-svcAlternatively, you can browse the repository and download an RPM file directly from https://package.perforce.com/yum/
Next
See the configuration steps in the Configuring section.
Installation script
If your operating system is not one of the Supported operating systems for package installation but is one of the Supported operating systems for the installation script, we recommend using the installation script rather than performing a Manual installation.
The installation script creates an operating system user account named perforce and a group named perforce for running HAS. Do not run HAS with the Linux root user account or Windows Administrator account.
Installation steps
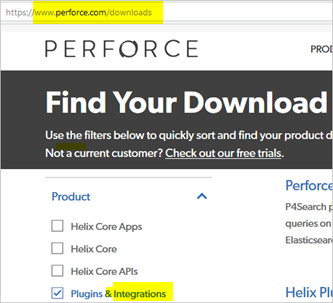
- Download Helix Authentication Service from the Perforce download page by selecting Plugins & Integrations.
- For Family, choose Platform Independent, select TGZ or ZIP, and Download.
- Expand the downloaded .tgz or .zip file.
- Verify that you now have a README file, an example.env file, and an install.sh file. The install.sh is the bash installation script.
- Verify that the bin subdirectory contains the configure-auth-service.sh file.
- Run the bash script named install.sh, which installs Node.js and then builds the service dependencies.
- Modify the service configuration by creating your own editing the .env file. Configuration consists of defining the identity provider (IdP) details for either OIDC or SAML, and setting the SVC_BASE_URI of the authentication service.
- (Recommended) For better security, replace the example self-signed SSL certificates with ones signed by a trusted certificate authority.
- Restart the service by using the systemctl restart helix-auth command. (The
systemctlcommand is part of the systemd process manager for Linux.)
When you type
./install.sh -h
the output is:
Installation script for authentication service.
Usage:
install.sh [-m] [-n]
Description:
Install the authentication service and its dependencies.
-m
Monochrome; no colored text.
-n
Non-interactive; does not prompt for confirmation.
-h | --help
Display this help message.
Next
See the configuration steps in the Configuring section.
Manual installation
If your operating system in not one of the Supported operating systems for package installation or Supported operating systems for the installation script, it might be one of the Supported operating systems for manual installation.
We recommend that you create an operating system user account named perforce and a group named perforce for running HAS. Do not run HAS with the Linux root user account or Windows Administrator account.
Easy way to install Node.js
If you are going to do a manual installation of HAS, a prerequisite is an installation of Node.js. Various packages for Node.js make it easy to install Node.js.
Installing Node.js on Ubuntu
| 16, 18, 20, 22 |
|---|
|
Packages from NodeSource are easy to install: $ sudo apt-get install build-essential curl git |
Installing Node.js on CentOS/RHEL 7
CentOS, Oracle Linux, and RedHat Enterprise Linux lack Node.js packages of the versions required by this service, but there are packages available from NodeSource that are easy to install.
$ sudo yum install curl git gcc-c++ make
$ curl -sL https://rpm.nodesource.com/setup_20.x | sudo -E bash -
$ sudo yum install nodejs
Installing Node.js on CentOS/RHEL 8
$ sudo yum install curl git gcc-c++ make
$ curl -sL https://rpm.nodesource.com/setup_20.x | sudo -E bash -
$ dnf --repo=nodesource download nodejs
$ sudo rpm -i --nodeps nodejs-20.*.rpm
$ rm -f nodejs-20.*.rpm
Installing Node.js on RedHat Fedora 31
This release of RedHat Fedora provides a compatible version of Node.js, so installation is simple.
$ sudo dnf install nodejs
CentOS/RHEL 7, 8, RedHat Fedora 31, Ubuntu 16, 18, 20, 22
- Make sure you have an installation of Node.js, version 20 or later (see Easy way to install Node.js ).
- Perform the step under Installing Module Dependencies.
Other Linux distributions
- Download and install the Linux Binaries for Node.js, version 20 or later, making sure that the bin folder is added to the PATH environment variable when installing and starting the service.
- Perform the step under Installing Module Dependencies.
Windows 10 Pro and Windows Server 2019
- Download and run both:
- the Windows-based installer for Git because it is a precondition for installing Node.js
- the Windows-based installer for Node.js LTS
- Perform the step under Installing Module Dependencies.
Note that Windows native toolchain, available by installing the Chocolatey Windows package manager, is not required for the authentication service.
Windows as a service
If you want HAS to run automatically as a service, see Windows service installation.
Installing Module Dependencies
The following command copies dependencies from the Node.js package site into the node_modules directory within HAS. Open a terminal window and change to the directory containing the service code, then run:
$ npm install
- Download Helix Authentication Service from the Perforce download page by selecting Plugins & Integrations.
- Expand the .tgz or .zip file you downloaded.
- Verify that you now have a README file and an ecosystem.config.cjs file.
Windows service installation
The Helix Authentication Service can be deployed to Windows-based systems, and managed as a Windows service. The guide below outlines the installation and configuration process.
Installation
Prerequisites
Download and run the Windows-based installers for Git and Node.js LTS. Note that the native tool chain, available with the Chocolatey package manager, is not required for the authentication service.
Installing Module Dependencies
Installing the module dependencies for the authentication service is done from a command prompt. Open a Windows PowerShell window (preferably as an Administrator) and change to the directory containing the authentication service, then run the following commands:
cd helix-authentication-service npm ci --omit=dev --omit=optional npm -g install node-windows npm link --omit=dev --omit=optional node-windows node .\bin\install-windows-service.js
If you run the commands as a normal user, as opposed to an administrator, several User Access Control prompts from Windows will request your permission for the installation of the service.
HAS is now installed and running as a Windows service. If the system restarts, the authentication service starts automatically.
If the service does not appear to be installed and running, run the uninstall script and then install a second time.
node .\bin\uninstall-windows-service.js
node .\bin\install-windows-service.jsStarting and Stopping the HAS Window Service
You can start and stop the HAS Windows service by using the Windows service utilities. The Services application provides a graphical interface for this purpose.
Alternatively, the net command can be run as administrator from the command shell:
To stop the service,
net stop helixauthentication.exe
To start the service,
net start helixauthentication.exe
Configuration
The configuration of the authentication service is managed through environment variables. An easy method for setting the variables for the service is with a file named .env in the directory containing the authentication service. The .env file is a text file that contains names and values, separated by an equals (=) sign. For example:
-
Stop the service.
-
Add these lines to the .env file:
SVC_BASE_URI=https://has.example.comLOGGING='file://C:\\helix-auth-svc\\logging.config.cjs' -
Start the service.
When specifying values in the .env configuration file, you can enclose the values in single (') or double (") quotes. For file paths, you can use a single backslash (\) or double backslashes (\\). The LOGGING setting requires the prefix file:// with double forward slashes.
For additional settings, see Configuring.
Logging
The output of the authentication service is captured in text files in the bin\daemon directory within the directory containing the authentication service. The error output is in a file named helixauthentication.err.log and the normal output is in a file named helixauthentication.out.log.
By default, basic logging of the service executable is written to the Windows event log in a source named helixauthentication.exe, which shows when the service starts, stops, or has critical errors. There might also be a second source named Helix Authentication wrapper that is created by the program that runs the authentication service as a Windows service.
The authentication service supports writing its own logging to the events log, and this can be enabled by configuring the logging. See the LOGGING section. To enable logging to the Windows event log, use the transport value of event, and optionally define additional properties, as described below.
| Name | Description | Default |
|---|---|---|
eventLog
|
Selects the event log scope, either APPLICATION or SYSTEM |
APPLICATION
|
source
|
Label used as the source of the logging event | HelixAuthentication
|
An example of logging all messages at levels from info up to error, to the SYSTEM events log, with a source named Auth-Service:
module.exports = {
level: 'info',
transport: 'event',
event: {
eventLog: 'SYSTEM',
source: 'Auth-Service'
}
}
Be aware that some versions of node-windows might send all logging to the Application category in the event viewer, despite the value of the eventLog setting above.
Removal
To remove HAS as a Windows service, open the PowerShell and execute the following commands from the installation directory of the Helix Authentication Service.
net stop helixauthentication.exenode .\bin\uninstall-windows-service.js
The Windows service can also be stopped from Windows' Services application, where its name is Helix Authentication, however uninstall-windows-service.js must still be run from the shell.
Next
See the configuration steps in the Configuring section.