Blog
October 14, 2020
Multi-Factor Authentication (MFA) is essential to help secure enterprise users and access to their data. Here we explain what is MFA and provide examples of multi factor authentication.
Follow along or jump to the section that interests you the most.
➡️ Get Free Version Control Tools
Back to topWhat Is MFA? And Why Is It Important?
MFA (Multifactor authentication) is an authentication method that requires users to verify identity using multiple independent methods. Instead of just asking for a username and password, MFA implements additional credentials. MFA is important because it makes stealing personal information more difficult.
What is MFA? MFA is the easiest and most popular way to secure enterprise users and access to their data. Additional verification credentials must be met using information from the following categories:
- Something the user knows.
- Something the user has.
- Something the user is.
What Is the Purpose of MFA? Multi-Factor Authentication Examples
Examples of Something the User Knows
Knowledge factors are the most common — and vulnerable — type of security. Knowledge factors are less secure because the information is easier to share or steal. A multi-factor authentication example of something the user knows could include:
- Passwords.
- PIN (or personal identification numbers).
- Answers to supposedly secret questions (such as “Where were you born?” or “The name of your first-grade teacher.”).
Examples of Something the User Has
Something the user has — also called possession factors — have been the foundation of security for centuries. The most basic version is a key, which opens a lock. Possession factors are more complex now, but the premise is the same. A multi-factor authentication example of something the user has could include:
- Google Authenticator (an app on your phone).
- SMS text message with a code.
- Soft token (also called software token).
- Hard token (also called hardware token).
- Security badge.
Examples of Something the User Is
A biometric verification (or something the user is) is a way to identify a person using their unique biological traits. Examples of biometric verification include:
- Fingerprint.
- Palmprint.
- Voice.
- Retina and iris patterns.
- Signature.
- DNA.
How Multi-Factor Authentication Works
The goal of MFA is to provide a multi-layered defense system. This helps ensure that the users who access your system are who they say they are. Even if one factor is compromised, there are still more barriers to breach. For example, if someone’s computer password is stolen, the thief would still need more than just that information to break into the account.
81% of data breaches involve weak or stolen credentials. MFA can prevent that. (Data from the 2017 Verizon Data Breach Investigative Report.)
With MFA, users need to have the correct combination of multiple authentication factors. For example, to log in to a secure program, a user might need to type a password (something the user knows) and enter a number from a hard token (something the user has). Only the correct password combined with the correct number from the correct hard token would give a user access.
Back to topMulti-Factor Authentication Meets Version Control
Large companies use multi-factor authentication to limit access to mission-critical systems. Health care systems use MFA to ensure protected health information (or PHI) stays secure. And many smaller businesses use MFA for email because it helps keep phishers out.
Version control software often stores some of the most valuable assets companies possess — their intellectual property. However, most version control systems don’t provide full 360-degree support for MFA. For example, some version control tools have two-factor authentication (or 2FA) in their web interfaces, but not on the command-line. This setup leaves IP exposed.
When MFA isn’t used, any malicious person can pull down an entire repo from the command line. The only thing they would need is a username and password.
Incredibly, 42% of companies have experienced ransomware attacks. Exfiltration by disgruntled employees is a real issue. And careless or distracted employees can fall victim to phishing scams, exposing your assets to the world.
Mission-critical applications are protected with multi-factor authentication (or MFA). But what protects your IP — especially the code that’s stored in your version control system?
Back to topGet Enterprise-Grade Protection
If you're using Helix Core for version control, it can protect your IP. Not using Helix Core yet?
Why MFA Is Important In Version Control
Version control systems store some of the most valuable assets companies possess — their intellectual property.
Some VCS have 2FA (two-factor authentication) in their web interfaces, but not on the command-line. As a result, IP is left exposed. This means that with only a username and password, someone could pull down an entire repo from the command line.
📘 Related Resource: How to Lock Down Git
Back to top
What Is MFA with Helix Core?
Support for MFA is available with Helix Core. When authenticating against a cloud-based identity provider via either OpenID Connect or SAML 2.0, Helix Core customers can implement MFA via the Helix Authentication Service (HAS).
HAS enables single-sign on across clients such as the Helix Command-line Client (p4), Helix Visual Client (p4v), Helix Swarm, and Helix Core plugins and integrations. Customers authenticating against cloud-based identity providers are encouraged to use the MFA capabilities offered by their identity provider during the standard authentication process.
Helix Authentication Service is internally certified with Microsoft Azure Active Directory (AAD), Okta, and Google Identity. It is also known to be compatible with other identity providers such as Auth0, OneLogin, and Google G-Suite.
Helix Authentication Service is supported by all Helix Core client software. For customers who have separated their password store and their MFA service (ex: LDAP for passwords, Okta for MFA), it is possible to still use the now legacy Helix MFA app. This solution utilizes a separate trigger for the MFA process.
How It Works
When users try to access the server from the command-line, visual clients, or plugins, they’re required to provide the additional authentication factors. These are configured by an administrator.
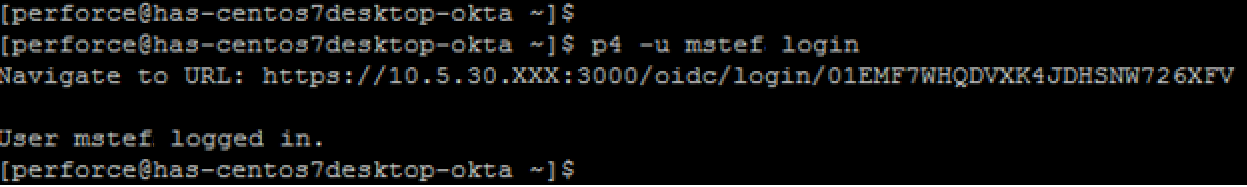
For example, when logging into the Helix Core Command-line client (P4), if the user does not already have a valid ticket, the command-line client will automatically redirect the user to their configured identity provider via the user’s default browser.
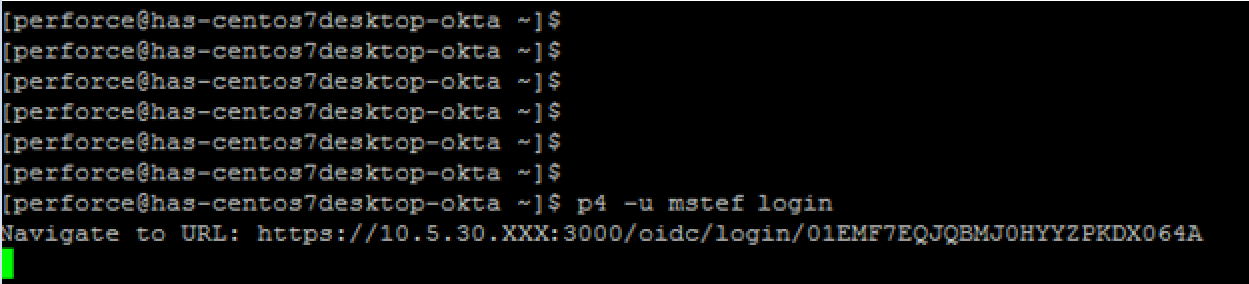
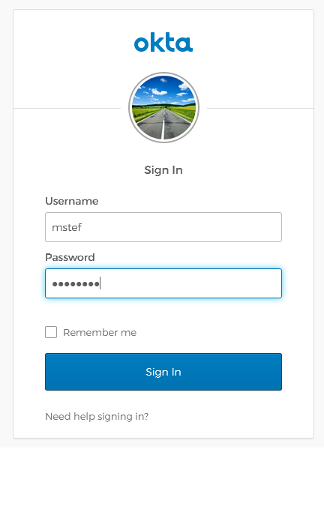
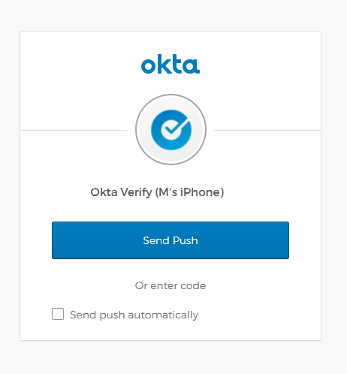
Assuming MFA has been enabled through the identity provider, the user will be challenged to prove their identity (in this case via something they have).
Assuming the user was able to prove their identity, a message displays in the user’s default browser letting them know that the authentication was successful.
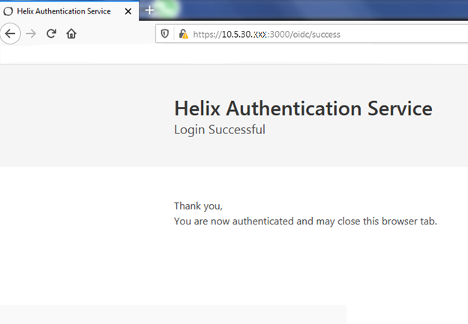
The user has now successfully logged in via the command-line.
 Back to top
Back to top
Get Started with MFA
Add MFA to your source code and digital assets. You can try Helix Core free for up to 5 users and 20 workspaces — and add MFA to your assets.
If you're already a Helix Core user, you can download Helix Authentication Service (HAS) for free to get started now.

