The severity and ingenuity of cyberattacks continues to increase as malicious actors become more proficient, breaking through the software layers and aiming to also compromise hardware like integrated circuits.
Relative to software, it is much more difficult to patch security vulnerabilities in integrated circuits (ICs) – making early identification of IP security weaknesses increasingly important.
We recently covered this topic in a joint webinar with OneSpin: A Siemens Business, where we demonstrated early security verification on a small module of IP intended for integration into an IC.
Back to topBack to topLearn How to Quickly Identify and Address Security Vulnerabilities
Our IP Security: Keys to Early Detection of Security Vulnerabilities webinar details best practices for IP security management and software patching, so your team can better prevent and defend against cyberattacks.
What Is the Goal of IP Security Vulnerability Detection?
The goal of detecting common vulnerabilities and exposures in IP security is to discover weaknesses early and keep them out of the final SoC.
A final system on chip design is a patchwork of IPs with various origins, quality levels, and attack surfaces.
To successfully assure IP security, mitigate security risks, and stop security threats, you need the right IP security assurance solution.
IPSA Security Information as IP Meta-Data
With Perforce IPLM (formerly Helix IPLM), everything is an IP – even the “Project” is just another IP in the system. This allows all IPs to be treated in a universal manner.
IP lifecycle management (IPLM) provides the ability to annotate rich meta-data on each IP object, which includes dependencies, permissions, hierarchy, properties, usage, and security information such as asset definition, attack surfaces, etc.
Depending on how security standards evolve, the definition and type of meta-data can evolve as well. This flexible system allows us to build out the standard and track the security information as IP meta-data, regardless of which IP is being used. Also, by attaching meta-data to different versions of the IP, we can analyze the changes in vulnerabilities over time.
In addition, since the security meta-data is attached to the IP (version), that IP can be used in a different context (or project) and carry this meta-data with it.
IP Asset and Vulnerability Generation
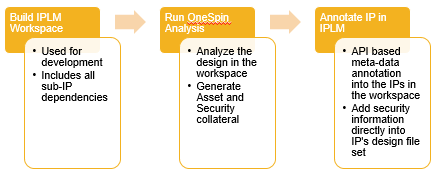
As illustrated below, the workflow begins with building IPLM workspaces. This builds out all the IP dependencies by checking out IPs in the hierarchical system Bill Of Materials from the various DM tools (Perforce P4, Git, DesignSync etc.).
From there, you can run a tool like OneSpin for analysis on the design files in the workspace. This extracts the security information and deposits it into the workspace in a standard format. Now, since IPLM knows the composition of the workspace, it knows which particular version of which IP should be annotated with particular security information.
From there, an API call is used to annotate the meta-data into the IPs in the workspace, adding security information as managed metadata in the IPLM platform. Users and integrators can now visualize and use the security information in the IPs they are consuming to build tests or otherwise guard against security vulnerabilities.
To better visualize this workflow, watch these tools in action the on-demand webinar here.
Back to topSecure Your IP
Early identification of security assets and threats is needed for today’s IP. This should start at the IP creation stage and be carried through the IP lifecycle by IP providers and integrators.
As demonstrated in the webinar, Perforce IPLM and OneSpin tools can enable the early identification of security threats, tracking, and verification to prevent weaknesses from making it into the final SoC.
To learn more about our solutions for IP security, connect with one of our IP experts today.
Learn more about Perforce ILPM
