Collaborate Without Borders with P4 in the Cloud
Perforce P4 (formerly Helix Core), the industry leading version control system by Perforce, empowers teams to accelerate innovation and collaborate at scale. Give your global team the power to store, version, and collaborate securely on all of their digital assets — from source code to media and 3D files — without sacrificing performance.
Cloud Deployment Options for P4
All of our cloud options offer the same industry leading version control, deployed your way.
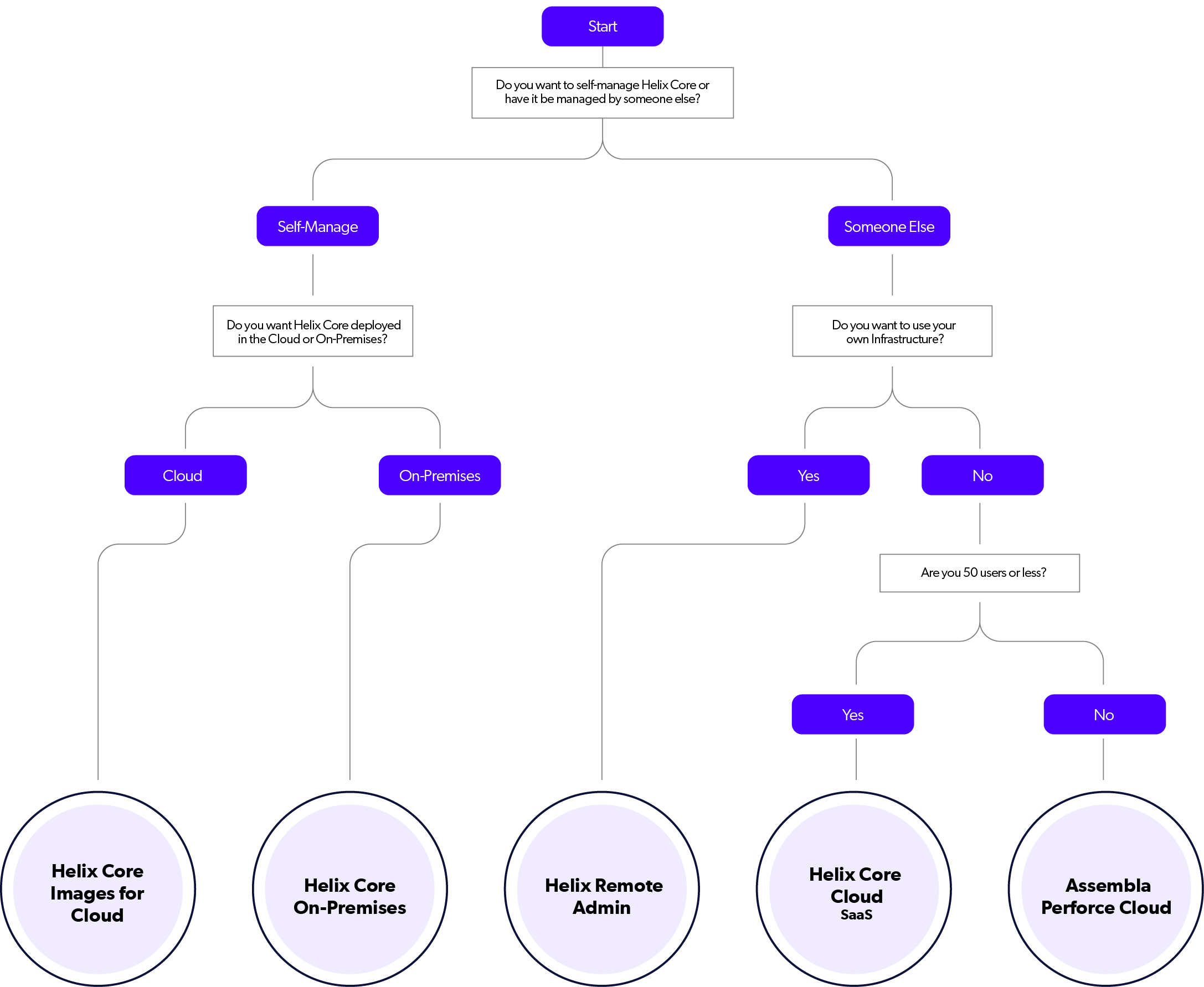
P4 Images for Cloud
- Turnkey, pre-installed instance of the P4 server.
- Available on AWS, Azure, Google Cloud, and DigitalOcean.
- Free for up to 5 users.
- Option to purchase annual licenses, with full support, for teams of any size.
P4 On-Premises
- Self-manage your P4 server on-premises.
- Free for up to 5 users.
- Option to purchase annual licenses, with full support, for teams of any size.
P4 Remote Administration
- Ongoing maintenance and administration managed by Perforce.
- Launch with best practice configurations.
- Supports on-premises, hybrid, and cloud infrastructures.
- For teams of any size.
- Yearly subscription.
P4 Cloud
- Single tenant (dedicated virtual machine).
- Hosted and managed by Perforce.
- Up to 50 users, up to 32 TiB storage (64 GiB included).
- $39/User/Month.
- Monthly commitment.
Assembla Perforce Cloud
- Multi-tenant.
- Hosted and managed by Assembla, authorized service partner.
- Up to 100 users, up to 1 TB storage (1 TB included).
- $52.25/User/Month.
- Annual commitment.
Need a Fully Managed and Hosted Option?
P4 Cloud is the fastest path to the most scalable version control for teams under 50. It’s the same industry leading version control, now available as a fully managed and hosted offering by Perforce.
Need Help with Our Cloud Options?
Get in touch with an expert at Perforce to learn more about cloud deployment options for P4.
